From cryptocurrency transactions to NFT ownership records, blockchain has exploded as a disruptive technology powering innovations across industries.
But what provides the secure foundation enabling these groundbreaking applications? Cryptography.
Blockchain relies on advanced cryptographic techniques that allow impartial strangers to exchange value without mediators.
How amazing, right? In this post, we’ll decode the crucial role of cryptography in blockchain’s immense potential for life.
Together, we’ll uncover how encryption provides the trust and security for everything from smart contracts to decentralized identity.
By seeing blockchain through the lens of cryptography, you’ll gain a deeper appreciation for the ingenuity powering this world-changing innovation.
Let’s dig in!
Understanding Cryptography
Chances are you have heard the term cryptography – but what exactly does it mean?
In simple terms, cryptography refers to the art of securing information through complex mathematics.
This typically involves encrypting a message (converting information into secret code) and decrypting it back to readable form with a key.
The origins of cryptography date back thousands of years to when Julius Caesar encrypted military messages using simple letter substitutions.
But modern cryptography really emerged during World War II when mathematicians pioneered increasingly sophisticated ciphers to protect communications.
Today, encryption is the backbone for securing everything from online banking to email.
At its essence, cryptography and its encryption tools provide a way to securely share information without being intercepted by eavesdroppers.
This brings us to the booming blockchain technology, which changed the modern data landscape by enabling decentralized, distributed ledgers and peer-to-peer transactions without intermediaries.
Cryptography in Blockchain
Rock-solid cryptography is essential for a decentralized ledger like blockchain to work at scale between untrusted parties. Cryptographic techniques enable:
- Confidential transactions: Encryption protects exchange details.
- Tamper-proof data: Any changes are easily detected.
- Verifiable identities: Digital signatures confirm authentic participants.
- Consensus mechanisms: Protocols like mining provide agreement.
Without cryptography, there is no trust. Participants could falsify transactions, forge identities, and double-spend funds.
But, strong encryption safeguards integrity across the blockchain.
Let’s discover some of the core cryptography algorithms and concepts underpinning blockchain technology.
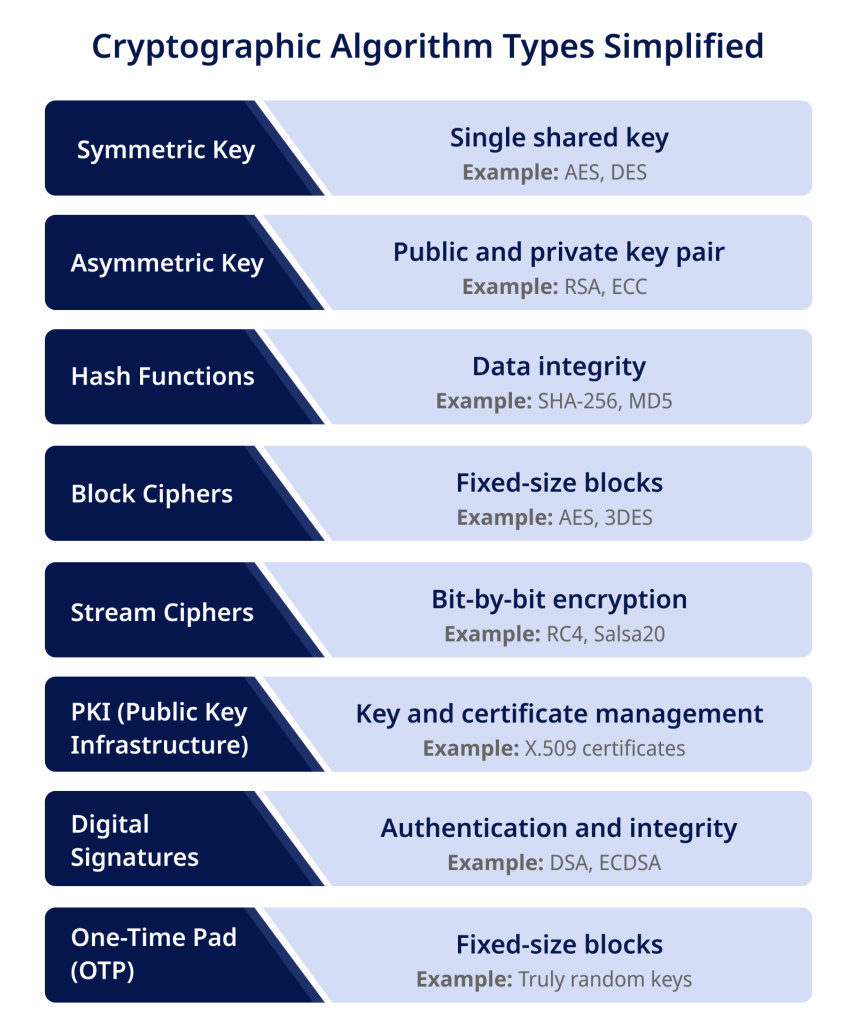
Types of Cryptography Algorithms
Blockchain relies on proven cryptographic algorithms to translate data into secure code and back again:
- SHA-256: This hash algorithm generates a unique fixed-length signature for any input. Used in Bitcoin to hash transaction blocks.
- AES: A symmetric encryption standard using keys to protect confidentiality. Secures wallets and dApps.
- ECDSA: Elliptic curve digital signature algorithm used by Ethereum to create digital signatures and public/private key pairs.
These represent just a few examples. New algorithms, like zk-SNARKs, use zero-knowledge proofs to validate transactions without revealing details, are also emerging.
The search for quantum-proof cryptography also continues as quantum computing looms.
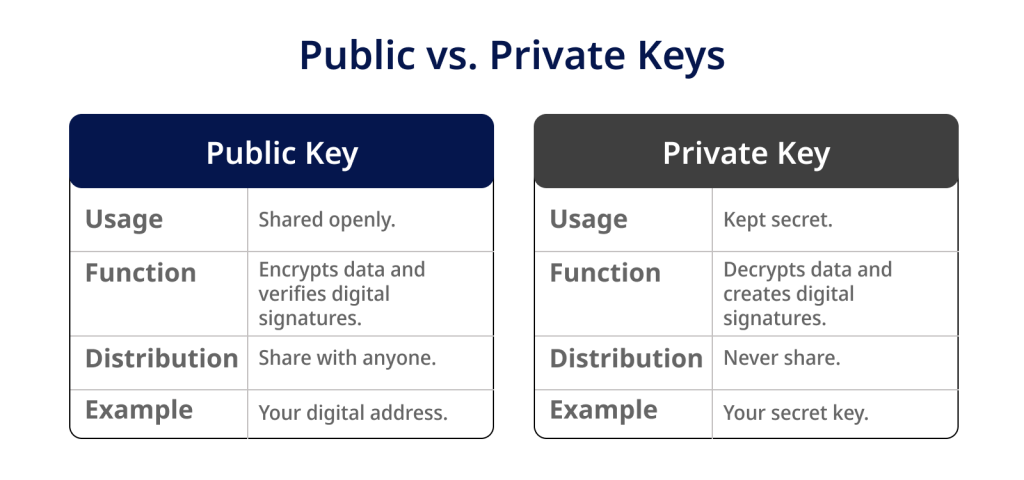
Public and Private Keys
Public and private keys are essential to asymmetric cryptography, a cryptographic technique widely used in blockchain technology and digital security.
Here’s a simple explanation of what public and private keys are and how they work:
- Public Key: A public key is like your digital address or a padlock that anyone can use to send you encrypted messages or verify your digital signatures.
It is derived from a complex mathematical process and is typically represented as a long string of numbers and letters. You can freely share your public key with others; it must not be kept secret.
- Private Key: A private key is like the secret key to your digital padlock. It’s a closely guarded secret that should never be shared with anyone.
Your private key lets you decrypt messages or create digital signatures that can be verified with your public key. Losing your private key can lead to losing access to your digital assets or compromised security.
Here’s how they work together:
- If someone wants to send you an encrypted message or verify your digital signature, they use your public key.
- They can’t reverse-engineer your private key from the public key; it only allows them to perform these actions.
- When you want to decrypt a message sent to you or create a digital signature, you use your private key, which only you possess.
- In the context of blockchain, public and private keys are used for securing cryptocurrency wallets.
- Your public key is your wallet’s address, which you share with others to receive funds, while your private key allows you to access and manage those funds.
- Keeping your private key safe is paramount to protect your digital assets and maintain security.
- Digital signatures also incorporate your private key to conclusively prove consent while maintaining the confidentiality of transaction details through encryption.
Digital Signatures
These digital signatures are cryptographic checks verifying blockchain transactions’ integrity and authenticity.
The math works like this: to create a signature, the transaction contents get hashed using the sender’s private key. The resulting hash gets attached to the transaction.
The recipient then decrypts the hash using the public key. If it matches the content hash, the signature proves the transaction came from the legitimate sender and was not altered.
This elegant math enables trustless verification.
Consensus Mechanisms and Cryptography
For a decentralized blockchain, consensus mechanisms like proof-of-work rely intensely on cryptographic puzzles and hashing power to achieve agreement on the ledger’s state.
By incentivizing nodes to competitively solve computationally intensive cryptographic problems for rewards, protocols like mining ensure it is economically disadvantageous for any single participant to cheat the system.
Cryptography enables detecting double-spend attempts and proving the computational effort nodes invested in verifying transactions.
Cryptography also hardens new alternatives like proof-of-stake to prevent attacks and falsification.
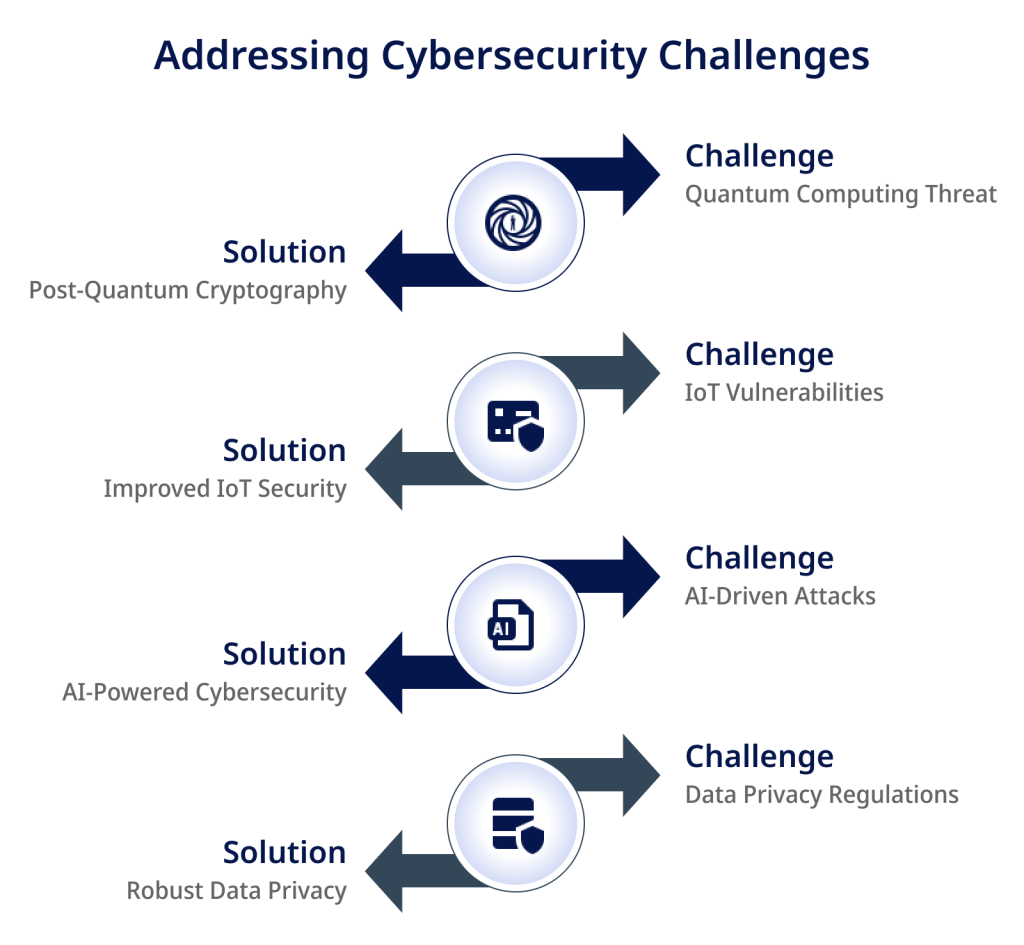
Ongoing Challenges and Advances
While the benefits of cryptography offer robust protection for blockchain today, challenges remain to stay ahead of emerging threats and technology shifts:
- Quantum algorithms threaten to break current public-key encryption. Alternatives like lattice-based cryptography seek to be quantum-resistant.
- Advances in AI may lead to more sophisticated hacking and cryptanalysis attacks. Defense research continues.
- Securely implementing cryptography also proves challenging. Flaws in random number generators or key management can expose vulnerabilities.
By keeping pace with research and examining any failures critically, blockchain cryptography continues evolving to meet new challenges.
Conclusion
Cryptography represents the lifeblood vitalizing blockchain and enabling its disruptive potential across industries. With advanced encryption securing identities, transactions, and consensus mechanisms, decentralized applications are possible. But blockchain also drives intense cryptography innovation – the two are deeply intertwined. New encryption algorithms, zero-knowledge techniques, and quantum-resistant cryptography push boundaries daily.
As blockchain permeates business and society, grasp its cryptographic foundations because security remains paramount in unlocking transformative possibilities through decentralized trust.